Malware is any software that disrupts computer operation, gathers sensitive information, or gains unauthorized access to private computer system. Once it gets a hold of your system, it will cause:
- Loss of productivity
- Embarrassment with customers
- Lost sales
- Lost data
- Substantial financial loss
- Frustration and loud swearing…

I’ve been getting questions about how malware infects computers. That made me realize that there is some misunderstandings that the general public has in this area. Certainly lots of information available via the web nowadays on this subject; however, most of the available information is intended for IT people and as such, this type of information requires a certain level of technical knowledge in the area of networks, computer systems, malware, etc. The available information is accurate, but most small business owners have limited time and/or interest in reading through pages and pages of technical information, much less following some and/or all suggested protection for computers.
I cannot really blame small business owners for shying away from reading all the gibberish (to them), that’s available about how to secure small business systems. Nonetheless, they must have some basic understanding of how malware can reach their business systems, in order to prevent getting malware on their computers. I’ll try to use common terms and simple explanations; hopefully, this won’t be that hard to follow…
The malware can reach a computer, laptop, tablet, smartphone in four different venues:
- Internet access, wired and wireless
- Internet browser
- Email clients, in the form of attachment and/or links
- Removable storage media, such as CD/DVD, flash drive, etc.
Statistically, 90% of malware reaches the IT equipment over the network while the remaining 10% is attributed to removable storage media. The typical unsecured setup, wired and/or wireless, for internet access would look like this:
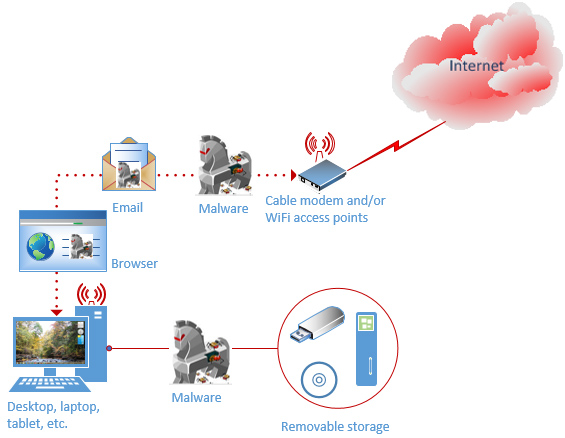
Unsecured small business/home system
Why is that important to understand this process? Well, knowing how your business systems may become victimized by malware will help you to prevent it. If knowing this information will simply make you more aware of how to use your small business system, that’s great.
The actual goal of this blog post is to assist in transitioning you from your current set up to a secure business system that looks like this:
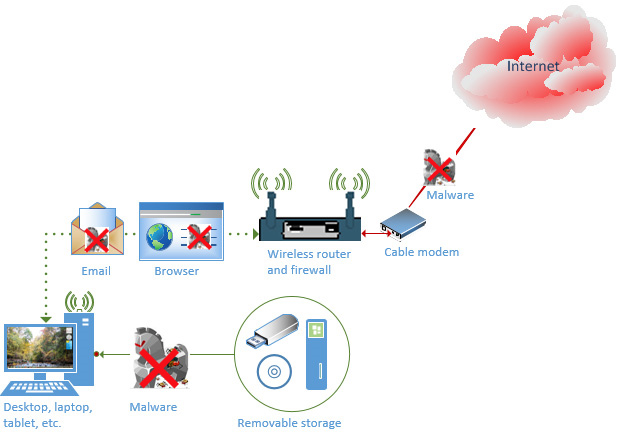
Secured small business/home system
The end result has accounted for all four potential weaknesses and removed and/or limited the impact of malware through these venues. Let’s take it step by step on how to eliminate and/or limit the way malware can reach the system.
1. Internet access, wired and wireless
Computer worms and automated scripts for hackers constantly scan the Internet for available services and exploit them automatically, if and when the vulnerable service is identified. For this reason, you should make sure that your computer or network is not open to this type of exploitation from the internet.
Adding a hardware-based broadband router and/or firewall remove the first major venue off the list. The cost for something of that nature would be around a hundred bucks. Something this simple can eliminate up to 10% of online risks through the Internet. The default factory configuration of the broadband routers blocks all Internet access to your system, in another word, just by installing one made your computers 10% more secure. Go ahead and test your computer at ShieldsUP! and confirm if your computer is at risk after you installed the broadband router. ShieldsUp! will scan your computer for available services at no cost. The result of this test should look like this:
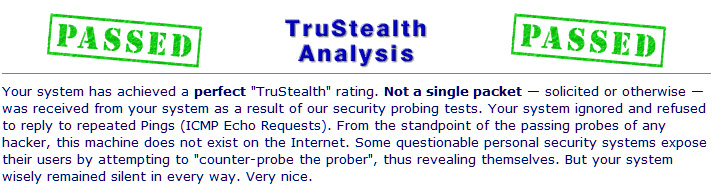
Stealth
Please keep in mind that the portable devices, laptops, tablets, etc., require a software based firewall, if and when connected to networks, that are not under your control.
If your system scan does not show the same result, adjust the firewall rules to match the result and/or contact me to do it for you.
Let’s move to the next venues to protect your system from…
2. Internet browser, 3. Email clients, and 4. Removable media
Protection against #2, #3, and #4 venues are principally the same:
2.1 Do not use an administrator account for everyday tasks, such as browsing the web and reading emails.
I do understand and somewhat agree that running your computer with an administrator account does make life easier, especially when the User Access Control or UAC warning disabled, but consider this. If you do that, you’ve just made the hackers/malware life real easy. When you’ve logged on to your computer with an administrative account, any programs that you’ll run will be running under this access rights. And that’s any program, even the ones that you’re not aware that is running in the background such as malware. Do you see just how easy you made it for the hackers? He or she does not need to find a way to gain access to the administrative account; you’ve already given it to them.
The administrator account can also disable the antivirus solution to prevent protecting against the malware. You really should remove the administrator account access from your account that had been created when Windows was installed. Proceed with caution and don’t lock yourself out of your system. Create and administrator account first with a reasonable password for the purpose, name it whatever you want, log in with this account to test it first. Once the new account had been tested successfully, proceed to remove the administrative access for the account that you’ve been using. This step-by-step guidance, titled “How to change user account type in Windows…” can assist you performing this task.
If your program(s) require administrative level of access, you should consider replacing them. If that’s not an option, you’ll need to run the program via the “Run as…” option, that’ll grant administrative access just for the program in question and not the whole system. Alternatively, if you have the UAC enabled, Windows since Vista and later will popup a window for entering administrative credentials, if and when the program requires this access level/right.
2.2 Use caution in browsing the web and reading emails
This is how the majority of malware gets on your computer, about 80% of them. Both the browser and email based malware utilizes social engineering to convince the end user that they must perform some action. End users usually need to click on a link that downloads the malware and installs it. The convincing part can be as simple as offering nude picks of celebrities, or links to your financial institution sites, law enforcement warning, etc.
For social engineering sample and how to be cautious in reading emails, please see this link
Internet browsing on the other hand is a different story due to how the browsers work. All web pages are just scripts for browsers and they are executed under the logged on user’s access rights to the system. Browsing the web with an account that have administrative access to computer is asking for trouble, as explained above in “a.”. So, what can you do, other than not browsing the Internet logged on with an administrator account?
Common sense will protect you in most cases. Certainly, staying away from “shady websites” such as porno, pirated software, MP3 download, and similar sites, will avoid getting malware on your computer. It would nice that this avoidance would secure you from malware, but that’s not always the case. Hackers are smart and know that most people intentionally do not go to these shady sites. As such, they hack legitimate websites and place either their malware and/or link to their malware at these sites. This is called “watering hole” based attack, where the end users don’t suspect that the legitimate sites will install malware on their systems. The legitimate sites that had fallen for this type of malware distribution and they still do. CNN and Facebook are probably the most commonly used websites that had fallen to this malware distribution. Protecting against watering hole based malware is covered in “2.3.” below.
2.3 Keep the operating system and applications updated
Most, if not all malware takes a hold of your computer by exploiting known software vulnerability. Software companies do release updates to remove this vulnerability and you should install it as soon as they become available, be that for the Windows operating system and/or applications installed on your computer. Nowadays, most software has an automatic update feature that will download and install the updates automatically. You should not disable the automatic updates, let them update in timely manner, as they should, to prevent known vulnerabilities of the software to be used against your computer.
Don’t just trust the automatic update that it’ll do its job, sometimes they don’t. Since the majority of the malware reaches your computer through the browser, you should periodically test the security of the browser and its plugins at this link, a plugin installation required:
https://browsercheck.qualys.com/
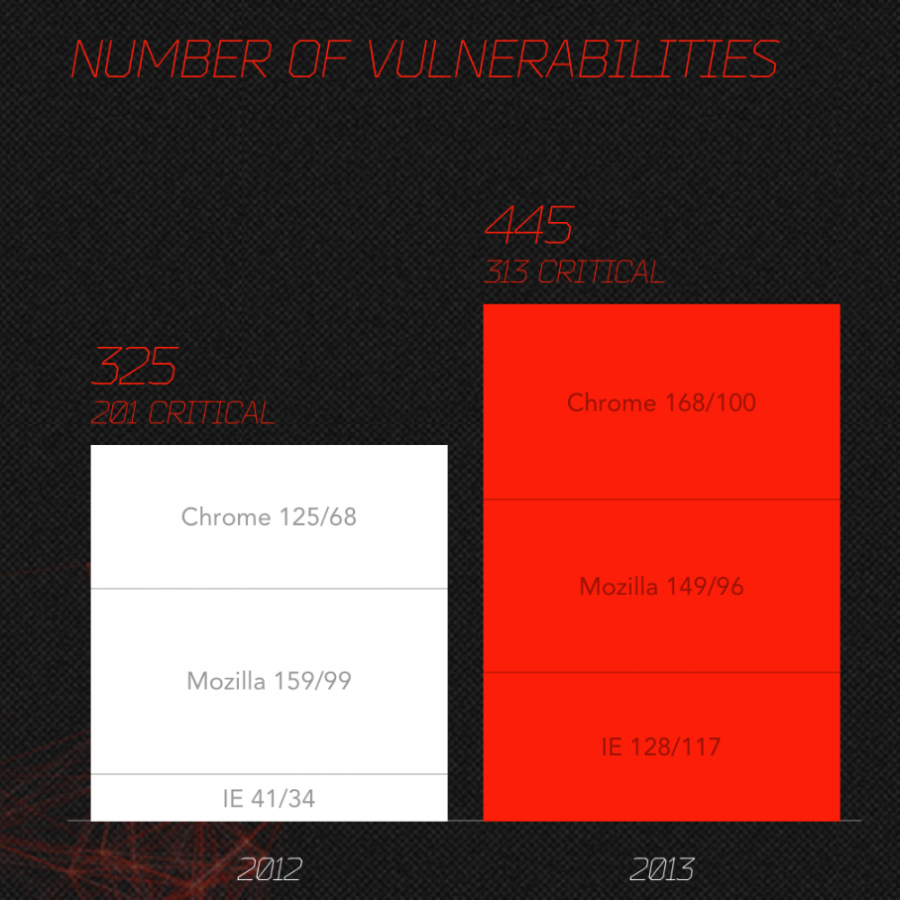
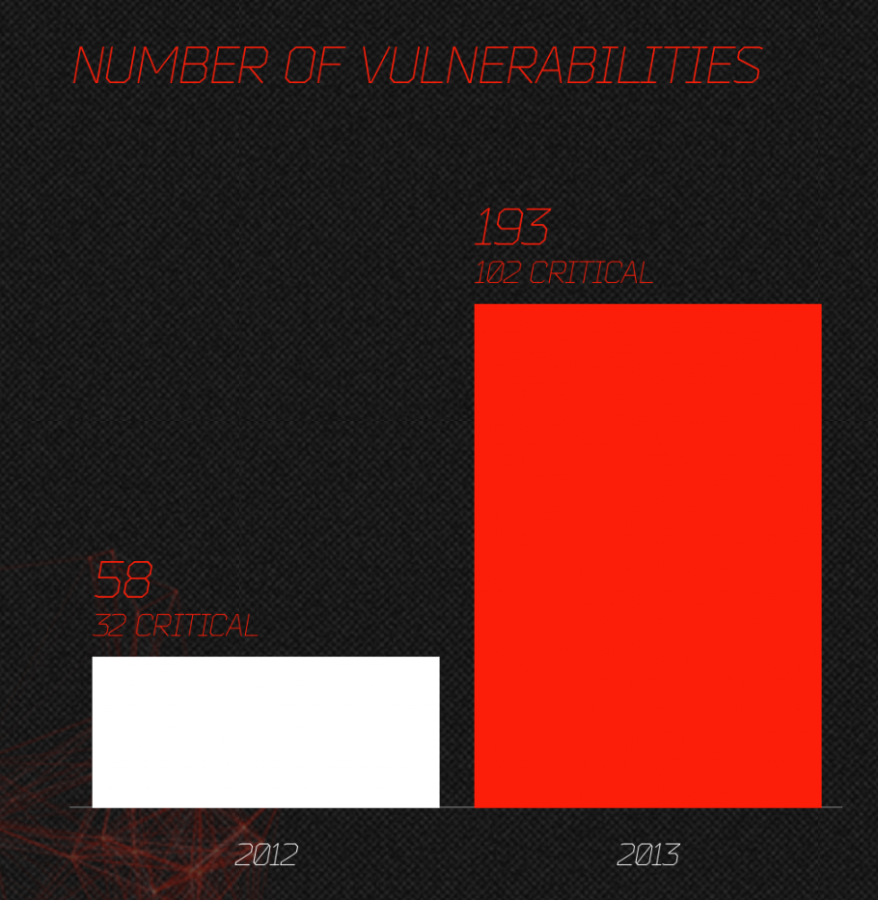
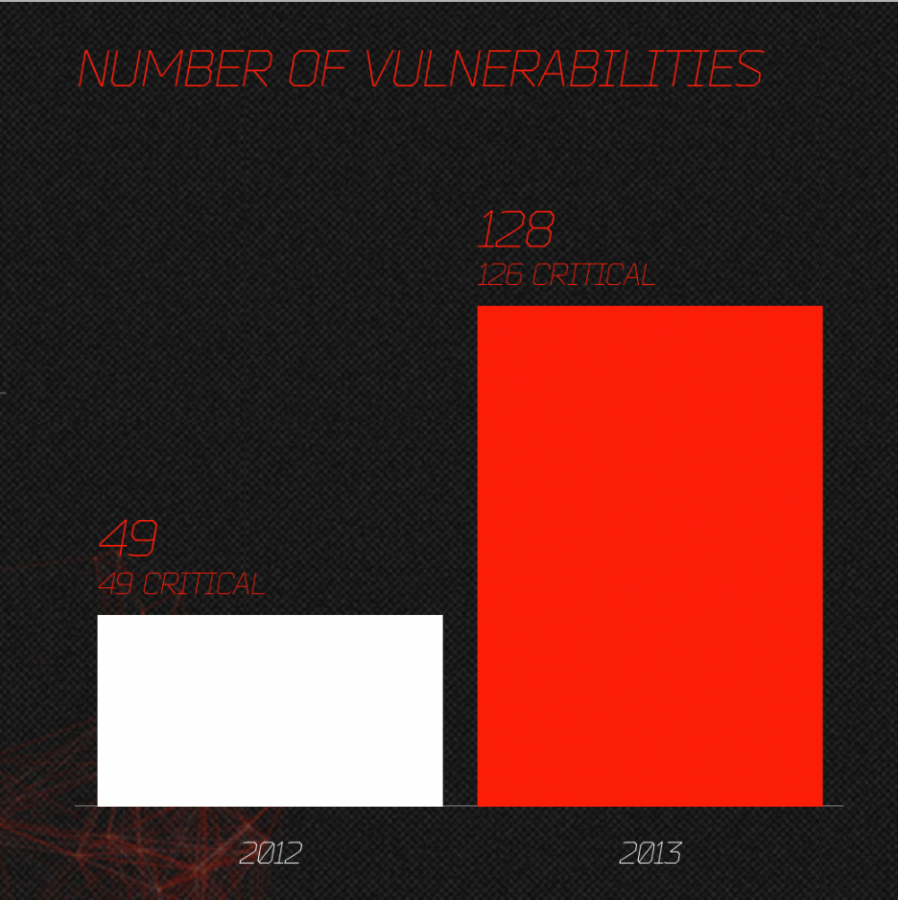
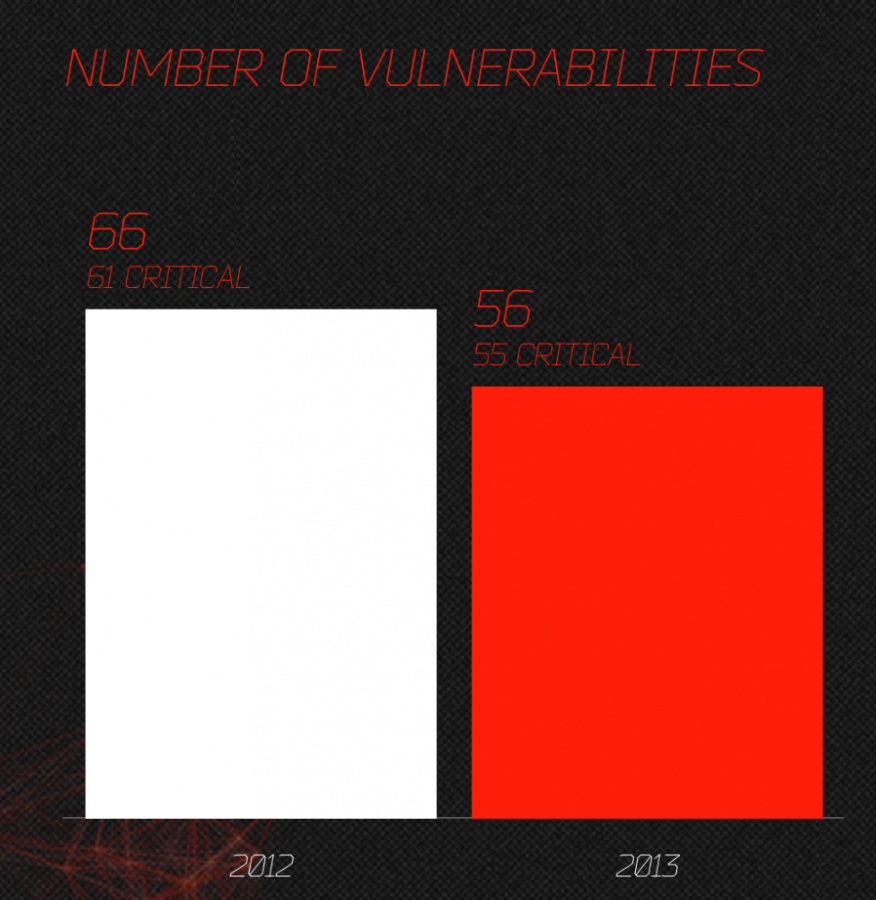
The Qualys plugin will scan your system for missing patches that includes browser, operating system and applications. The results displayed in your browser with links to the updates. Here’s the results for my system:
Browser:
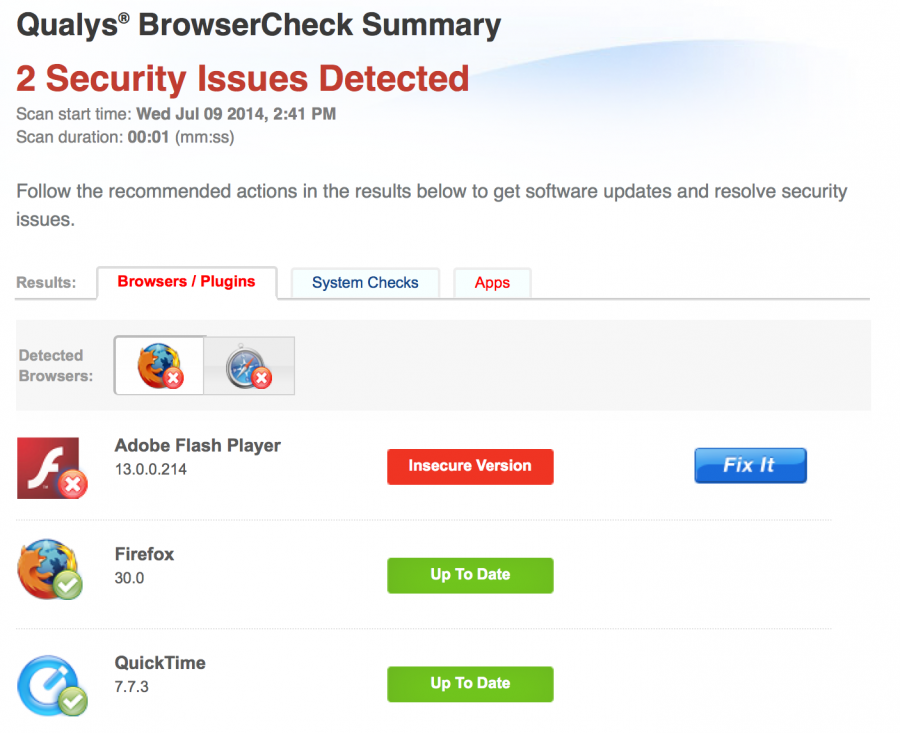
System:
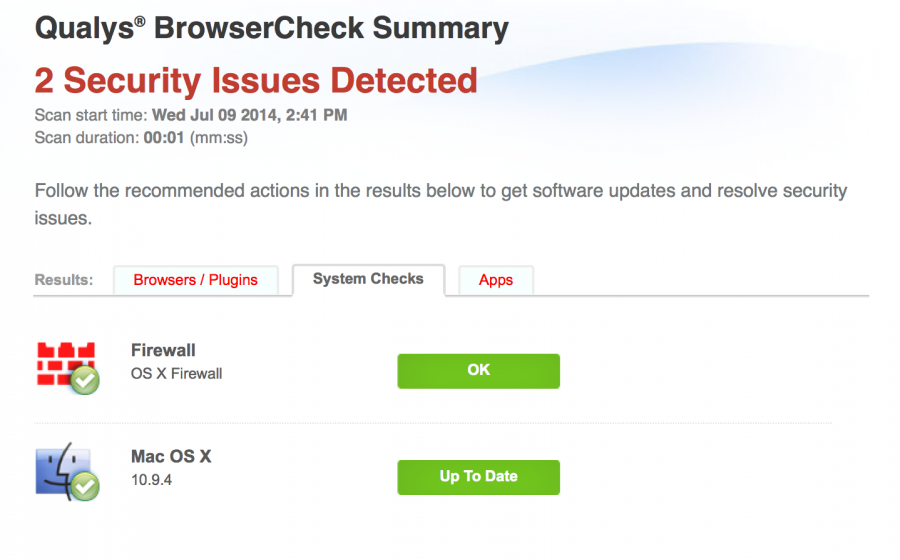
Applications:
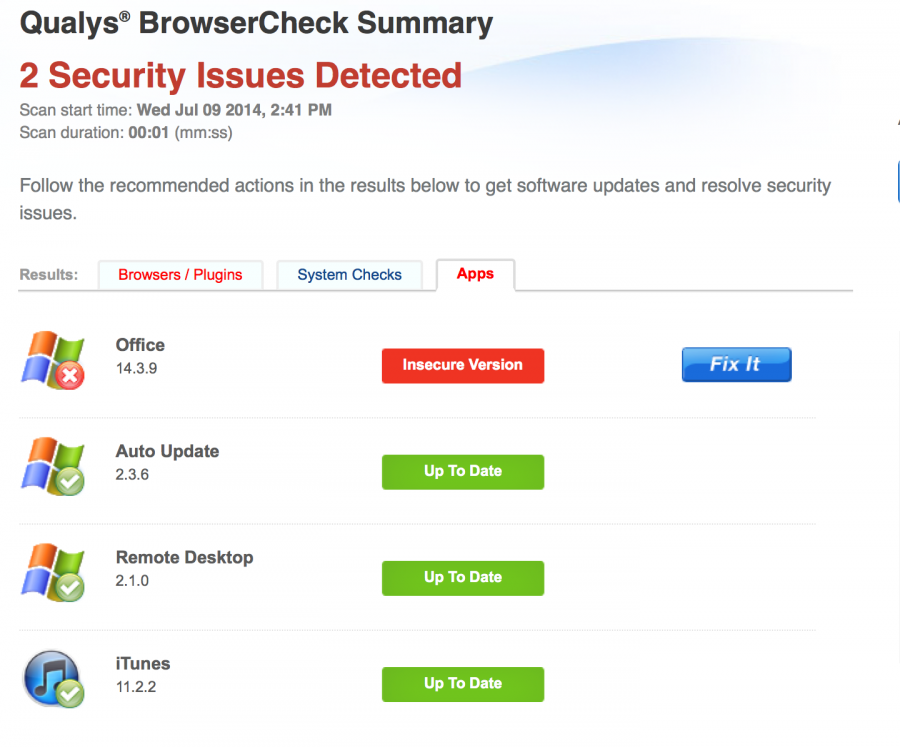
The computer missing updates is vulnerable to exploits, be that Windows PC or in this case an Apple computer. The latter one may not have as many malware as the former one, but nonetheless, it can be exploited just as well as Windows PCs if and when it’s missing updates.
2.4 Purchase and install antivirus product (approximated $50-80), update definition files frequently
This does not require much explanation, I hope. As long as you don’t use an administrative account for everyday tasks, it’s a worthwhile investment. You could also forgo purchasing an antivirus software and use Windows Defender, if you have Windows Vista or later version. The Defender is free with the operating system and provides protection against malware. The Defender and other antivirus effectiveness is greatly increased, if you follow the security recommendation in this blog.
2.5 Removable storage media
Generally speaking, most of the malware on removable media is rather old. An up to date antivirus will stop older malware from infecting your computers. Nonetheless, you should:
a. Disable “AutoPlay” for removable storage media:
In the “Control Panel” select “Hardware and Sounds”, click on “AutoPlay” icon, and select “Take no action” for software and games at the minimum.
b. Scan the removable media:
Your antivirus software by default will ask you, if you want to scan the removable storage media, just say yes…
Following these recommendations will protect you against most known vulnerabilities, about 95% and so far, it costs you about 175 bucks, some time to install, and configure the components.
So, what about the remaining 5%, how does one protect the system against that?
There are other options that can increase protection of the system with additional software. Knowing that sophisticated malware, among other malware, utilizes buffer overflow technics; you need a solution that will protect against this technology. One such software is Microsoft Enhanced Mitigation Experience Toolkit, or EMET for short. This protection is free from Microsoft and easy to configure and just by selecting the default option during installation, it will protect your system against most of the malware relying on buffer overflow technics.
You can also download and install Winpatrol – Scotty for free, which will monitor changes to Windows startup environment. All malware will change this environment and Winpatrol will alert you, if and when the startup environment is about to change. You’ll have the option to deny or allow the change.
With the additional protection installed, your system is protected against 99.9% of malware, provided that you have done and remain committed to following the steps in this blog post. That’s not bad for 175 bucks and some of your time invested. This is pretty much the best that someone, who is not an IT professional can do in today’s environment. Corporations spend millions of dollars, thousands of hours on installation and training, yet they are struggling to get to this level of protection.
If you have gotten this far, that’s great. You’re on your way to have a home/small business system, that will resist most, if not all malware trying to exploit your systems.
This seems complicated, but if you break it down and do one step at the time, apply some patience, it can be done by most computer users. If you run into trouble you can always re-read part of my blog, or contact me for help.
Alternatively, if you are short on time, you should hire BITS to do it for you. Contact Otto via email, or call the office at 203.569.7610. Based on your business needs dictated operational requirements, we can tailor a security protection for you.
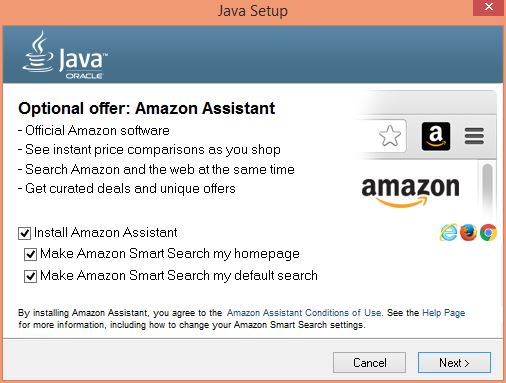
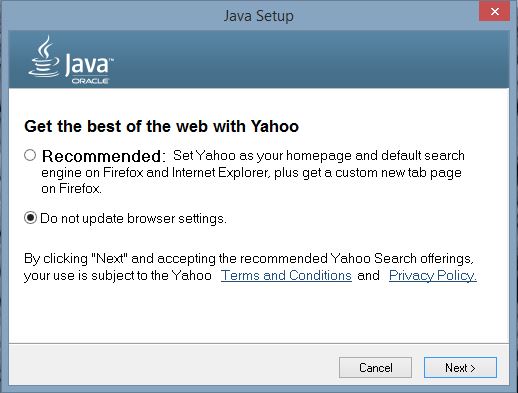

 As a result, the Java update failed notice is displayed:
As a result, the Java update failed notice is displayed: