The basic definition of malvertisement is:
infected online advertisement.
The legitimate website is supporting its operation cost by displaying adds from advertisement clearing houses. The actual add is downloaded in the background by your browser and the content of it is loaded, usually on the right side of the main content, but can be anywhere, including popping up the ad.
The ads can be useful for some people, but mainly annoying to others. It’s a business model where you receive “free” content and the website in question earns money to operate the site. You don’t necessarily need to click on the link in the ad to generate income for the website, just displaying the ad earns income for the website. The size of the income does increase, if and when the visitor clicks on the ad.
So, what’s wrong with this business model? The short answer is… nothing. The long answer…
The advertisement clearing houses collects potential clients, pretty much in discriminatively since their income depends on clients advertising products. Clearing houses also sell the client advertisement to other clearing houses, in addition to advertising companies selling it to these clearing houses. The cross selling is mainly due to the clearing house clients, some have more than others and in targeted advertisement it is important which website(s) will display the ad(s). As such, by the time the advertisement makes its way to the website, the actual ad could be originating from US, Europe, Asia, etc., and may have been going through 6-10 online advertisement companies.
The problem is that neither of the companies, including the website where it’s displayed, check the content of the advertisement for malware. As such, hackers love this venue for distributing their malware. They can create their ad, including malware, that may mimic legitimate products, and purchase advertisement time at the targeted website through the advertisement clearing house network. While the link is in their ad, you don’t need to click on the link to have the malware executed. It will load in the background as the website in question loads and in five minutes flat, your system is compromised.
So, what can you do against malvertisement based attacks? After all, like most people, you cannot give up visiting favored sites…
Notifying the website in question doesn’t do much good, especially after your system had been infected by the malware. The best a notification can achieve is that the malvertisment will be removed from the website, that will prevent other people getting their systems infected. Hackers will just purchase ad time with different fake brand name, may use the same malware, or create a new one.
Antivirus isn’t provide much of a protection against malware in advertisement, since the malware utilized isn’t know as of yet. Once it is known and blocked by antivirus, the hackers will create a new malware, and the perpetual cycle of unknown to known malware begins…
So, does that mean that there isn’t really much one can do, other than not using the internet? No, not really….
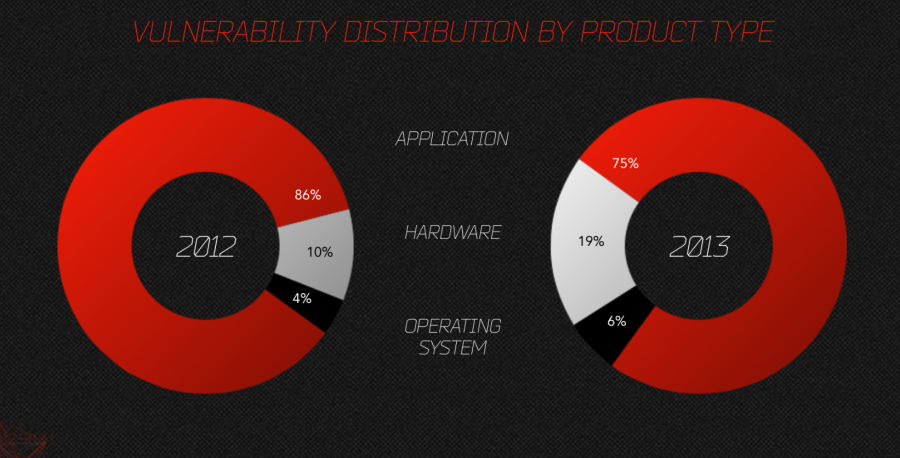
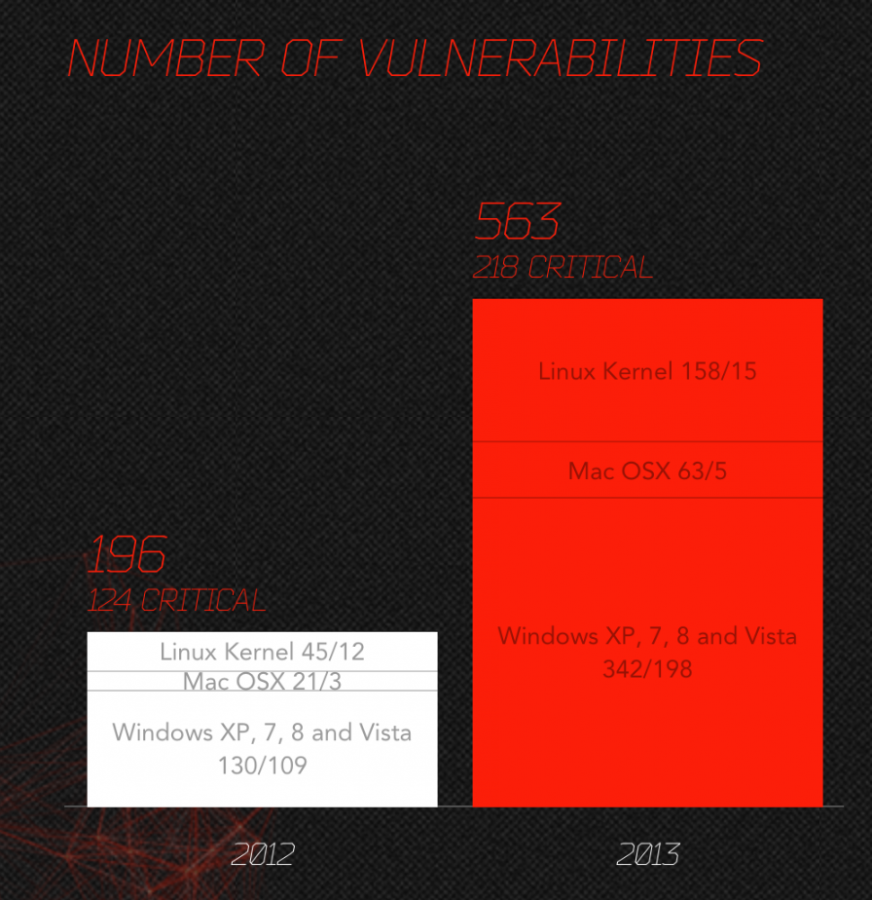
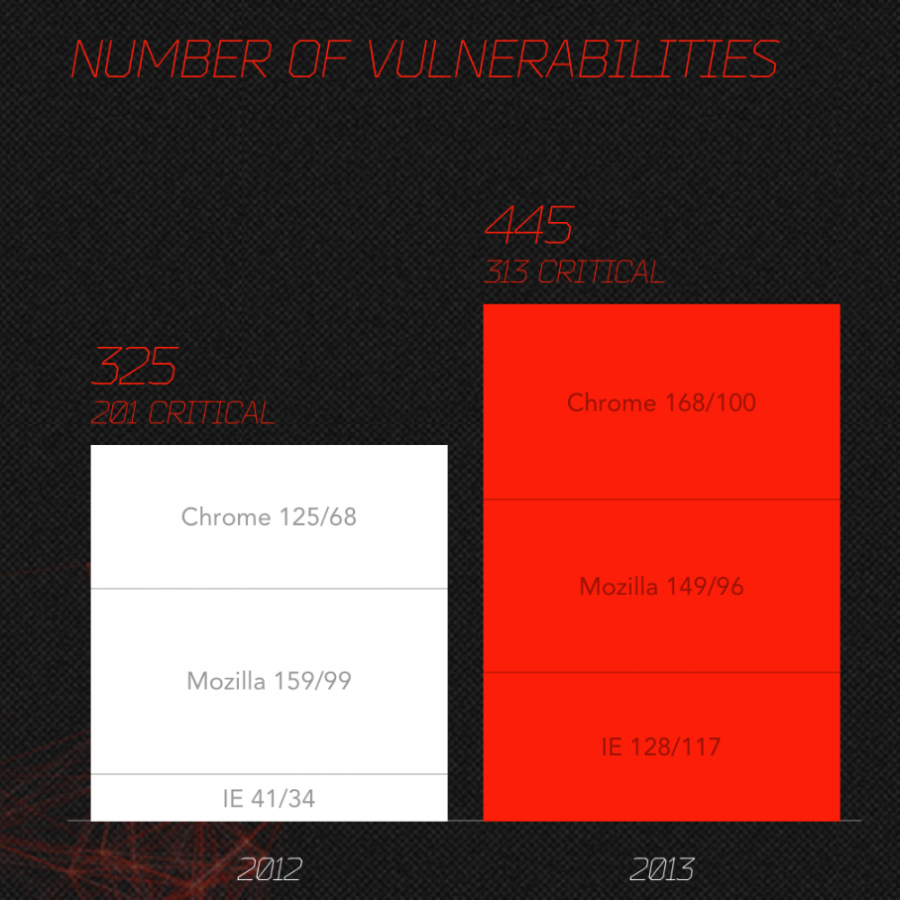
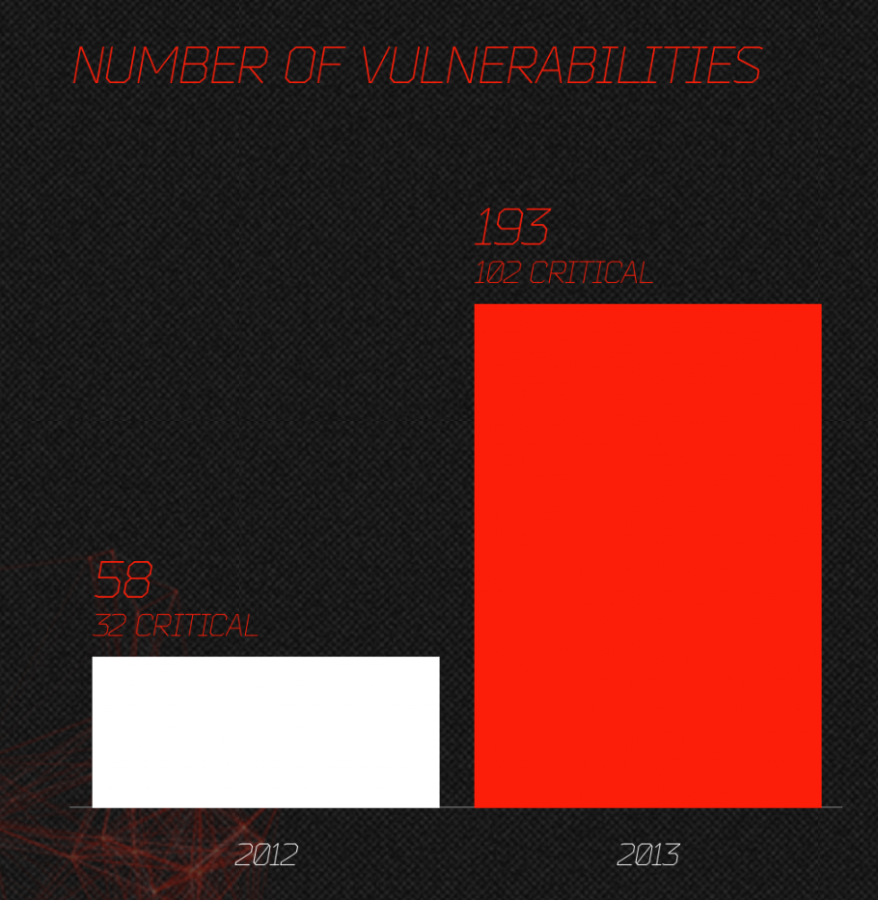
Let’s look at how the malware works in the malvertisement. The “payload” in the malware exploits known vulnerabilities in different applications. Different, as in most malware will try exploiting 3-4 different but vulnerable applications. Here’s a list of vulnerabilities that had been exploited in a recent malvertisement:
- CVE-2013-2551 (Internet Explorer)
- CVE-2014-0322 (Internet Explorer)
- CVE-2010-0188 (Adobe PDF Reader)
- CVE-2013-2460 (Java)
- CVE-2014-0497 (Flash)
The list above is a mixture of old and new vulnerabilities where the malware will try exploiting the applications. Once the exploit had been fully executed, the malware will stop processing the rest of the vulnerabilities. The order of list arbitrary in this blog, it does not indicate the actual order how the malware will process them.
So, what does this information tell you?
I can just hear you say, “I know, I know!”, and you are correct. Keeping your system and applications up to date will prevent most of the malvertisement or malware exploiting your system. Just keep doing it and you should be much better off than most people who do not…