Computer security can be complex and there are a slew of books available on this subject. They are well intended advises that work most of the times and for most people. The basic principal in these security advises include:
- Remove local administrator rights for the user account
- Only login as administrator account, if and when necessary
- Use strong password and change them periodically
- Keep both operating system and application patched all the times
- Implement layered security, don’t just rely on antivirus products
- etc….
These are all well intended and useful that can be verified by evaluating white/gray/black hats recommendations for mitigating exploits. Take for example Parvez’ posting on the subject of User Access Control (UAC) escalation, quote:
Office documents are opened in medium integrity so these are ideal targets to abuse the UAC bypass. Since these bypasses are so effortlessly achieved the only real course of action would be to set UAC to “Always notify” or remove local admin rights for the user. In the end, using agents like Microsoft EMET or MalwareBytes Anti-Exploit would be the best mitigating action to take from initially being exploited in the first place.
The fact that a gray hat, Mr/Ms Pervez, agrees with security experts should prompt you to follow their advise. So, you go ahead and add Microsoft EMET and MalwareBytes Anti-Exploit (MBAE) to expand your layered computer security protection. Since EMET is free for Windows OS and MBAE does have a free for home use version, it wasn’t too bad and you feel good about the added security protection.
Then one day, or rather frequently, Oracle’s Java update comes along and you install it. After all, keeping applications updated is one of the security advises. So, you download the file named “JavaSetup8u91.exe” from Oracle and use “run as administrator” to install it. The executed file will download additional files that will start installing the update. Well, first you’ll need to decide, if you want to allow additional software to be installed, like this one:
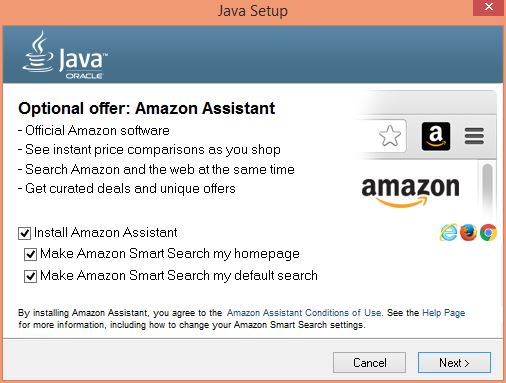
Or this one:
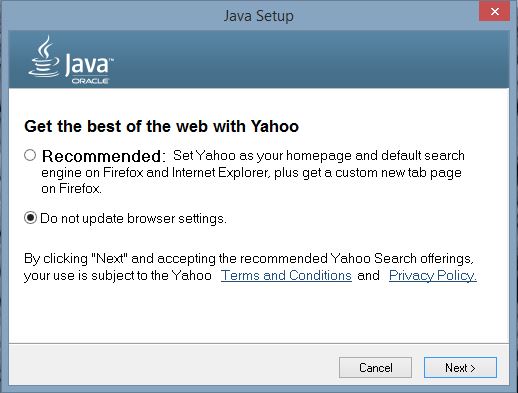
You can install these PUPs (Potentially Unwanted Program, or Potentially Unlimited Profits for Oracle depending on your view) or not, your choice. Now the Java update installation will start and displays the process status:

Let’s not start discussion about 3 Billion devices are vulnerable pretty much all the times, let the installation finish. Except that the newly acquired Microsoft EMET stops the installation with a popup message:
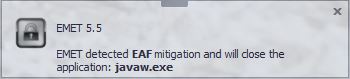 As a result, the Java update failed notice is displayed:
As a result, the Java update failed notice is displayed:
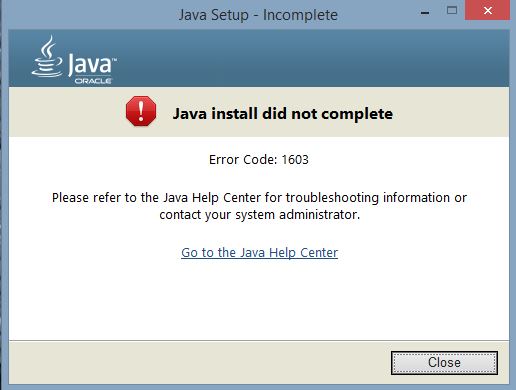
As a security conscious person, your initial reaction is “Did I just try to install some malware?” Or, is this just a false detection by EMET? You go ahead and check the download source, file properties, including the digital signature and everything looks just a OK.
Disable EMET for the time being and restart the Java update. That didn’t help, the installation still fails with error code: 1603. Then disable MalwareBytes Anti-Exploit and the installation still fails. As a last ditch effort, you disable the antivirus and finally, the Java update completes successfully.
Really Oracle? It’s not enough that Java is a popular target for malware, due to its less than ideal code base. What’s next, we will need to disable layered security protection just to enable Java to run on our computers?
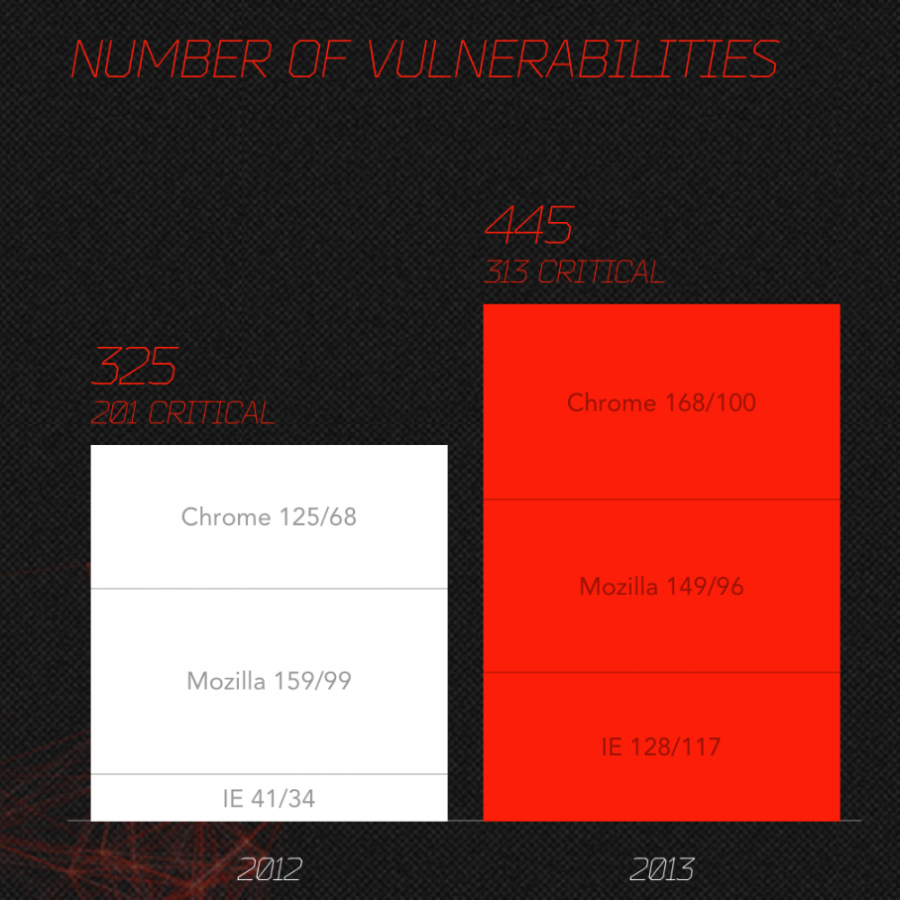
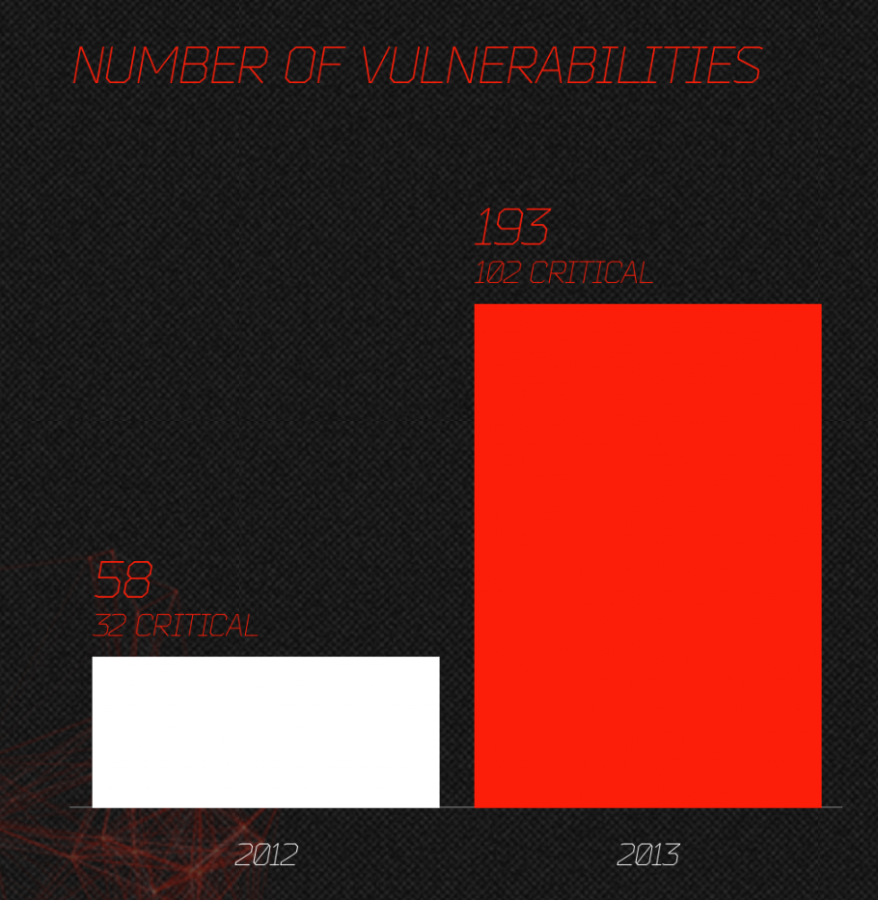
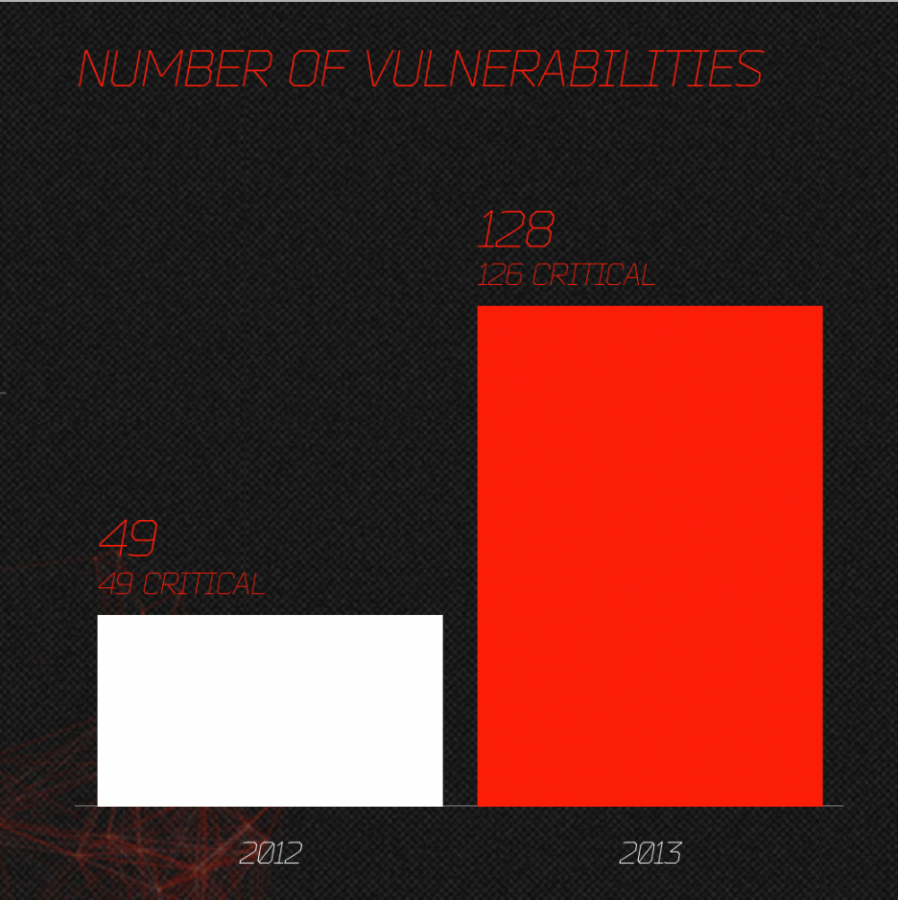
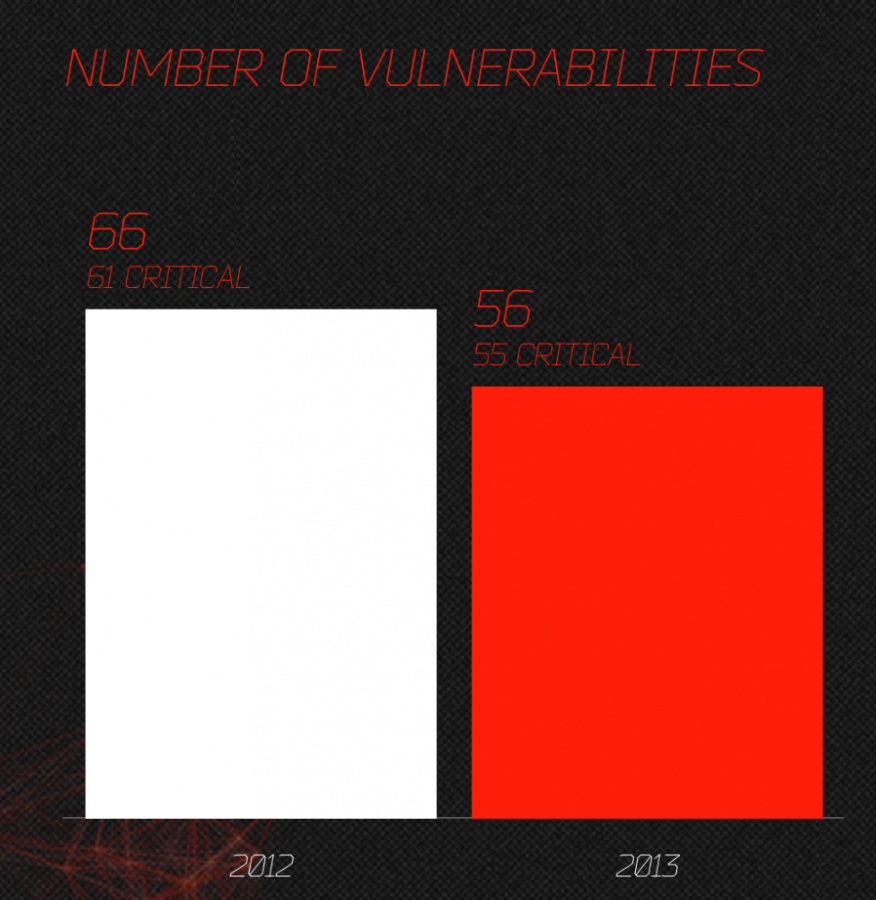
Maybe we should “start discussion about 3 Billion devices are vulnerable pretty much all the times” after all…