Threat Brief‘s “Daily Threat Brief, or DTB, is a daily open source intelligence report modeled after the concept of the President’s Daily Brief (PDB). Every day the analysts of Cognito succinctly provide insights into global risk and security issues in ways that can reduce your personal and business risks and inform your strategic decision making.” You can subscribe to receive email highlights of these reports on a daily basis, more or less useful for security people.
Threat Brief does not use their business email server to send out the daily briefs, smart, they subscribe to a service provider that tracks the links in the email that you’d click on :
http://threatbrief.us1.list-manage.com/track/click?u=xxxxxxxxxxxxxxxx&id=xxxxxxxxxxxxxx=xxxxxxxxxxx*
*-Actual tracking IDs replaced by x
That’s nothing new, this have been done on the regular basis. What’s new is that the list-manage.com site does not show the email clicked link in the browser, if the browser happens to be IE11, secured as it should be in addition to Ghostery blocking tracking script.
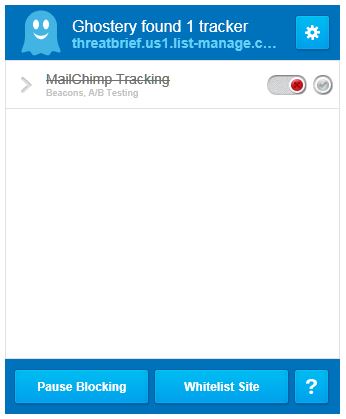
The tracking script is blocked by Ghostery is from MailChimp Tracking:
Cue the jokes about monkey business, etc… 🙂
While tracking isn’t necessarily a security risk for the most part, certainly can be, it is a threat for the privacy of the end user without question. Now, why would Treat Security utilize a third-party mass-mailer that results in privacy and potential security risks for the recipients of the Daily Threat Brief? That’s beyond me… Isn’t that a contradiction to the intended purpose of the threat brief?
After evaluating the “risk and security issues” of the employed tracking method for the daily threat emails, unsubscribe is in order. Fortunately, there’s an unsubscribe link on the bottom of the daily brief, let’s see how that one works…