Malware targets applications, hardware, and operating systems (OS) by exploiting known/unknown vulnerabilities in their software code. Why is that important to know? Well, knowing which components of your computer used for exploit is half of the battle in protecting your system. If you don’t want to read about this subject and just want to protect your system, here’s a shortcut for protecting against malware…; the link will take you to my blog on the subject…
Comparing malware introduced in subsequent years, in our examples below 2012 vs. 2013, will not just identify the main targets, but also show the direction that the malware heading. It should also remove some of the myth, that people have about system vulnerabilities… Let’s look at the target types first, shall we?
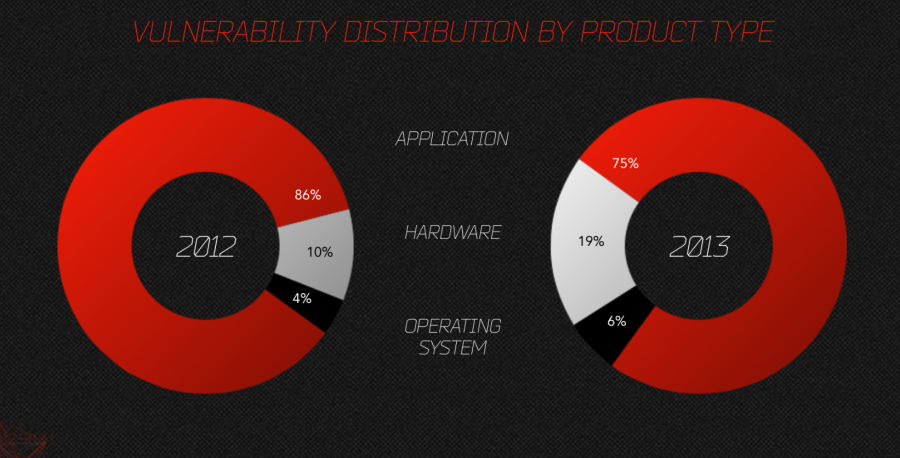
Image source: Netwar Project
Malware targets:
By and large, the applications are the most targeted software for exploits, followed by hardware and operating systems. Let’s leave the hardware out of this analysis, that’s another blog, and continue with the operating system platforms.
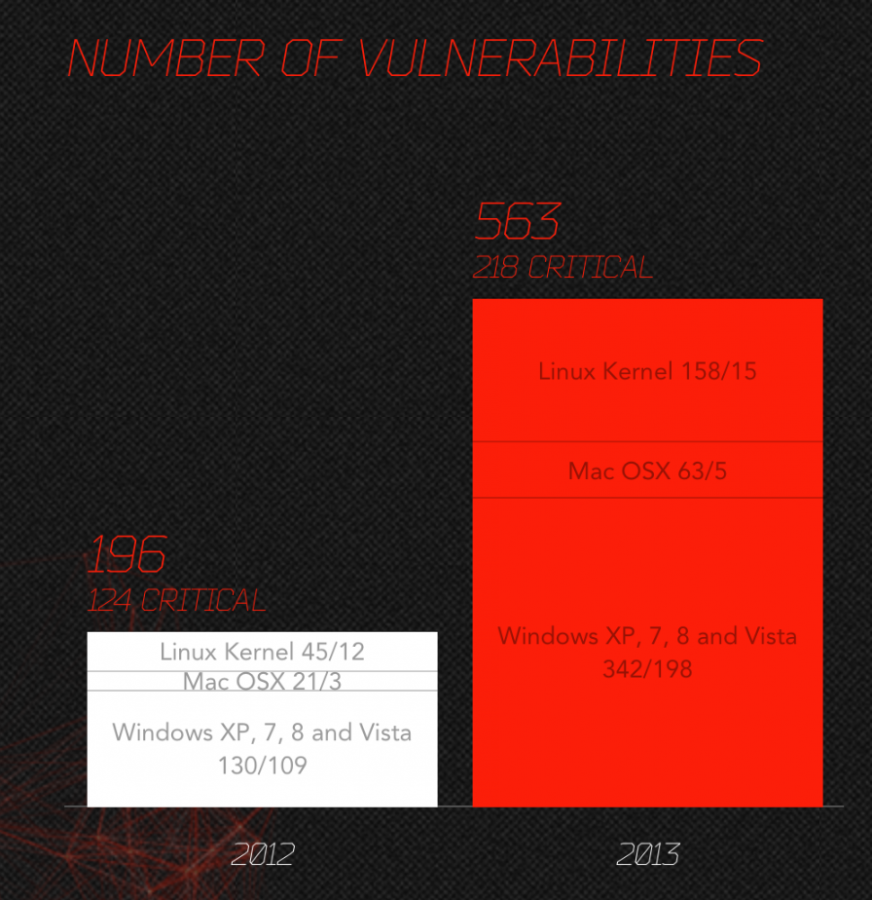
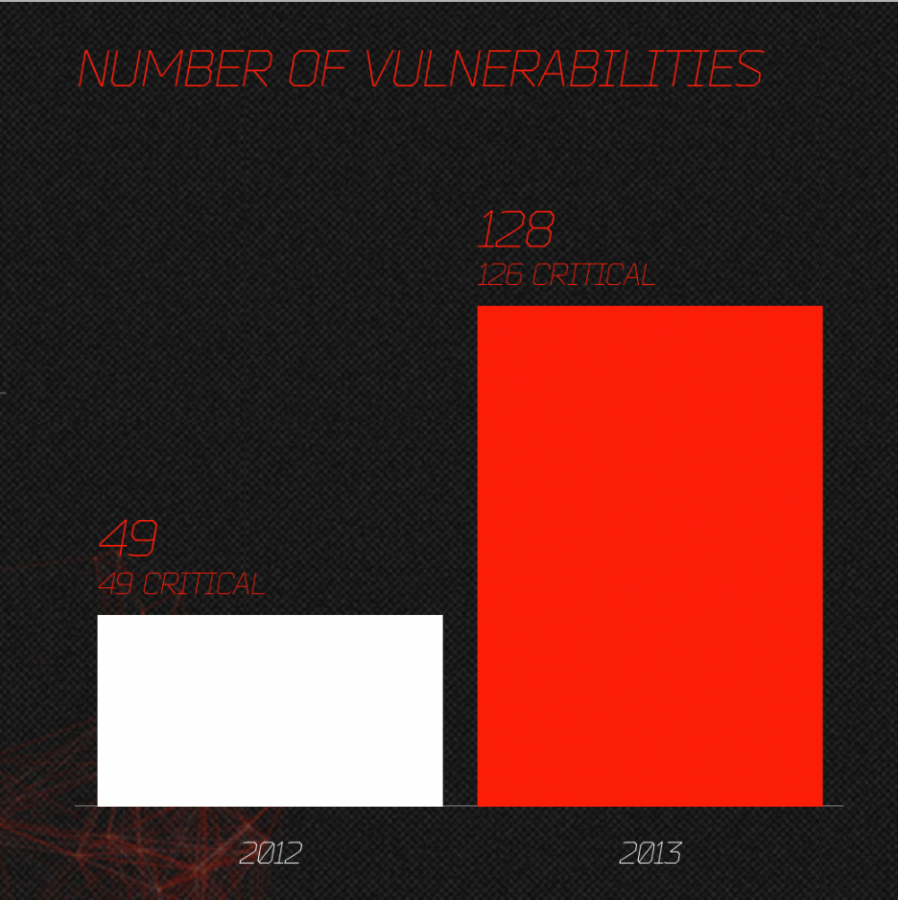
Operating system:
The operating system vulnerability had increased by close to 300% across all popular platforms, pretty much evenly. The number of critical vulnerabilities increase from year to year had been from 30 to close to 100%. The greater number of vulnerabilities for Windows platform is largely due to the greater operating system market share for Windows. Believe it or not, hackers do know about ROI (Return on Investment) and prefer to target Windows platform dues to its market saturation.
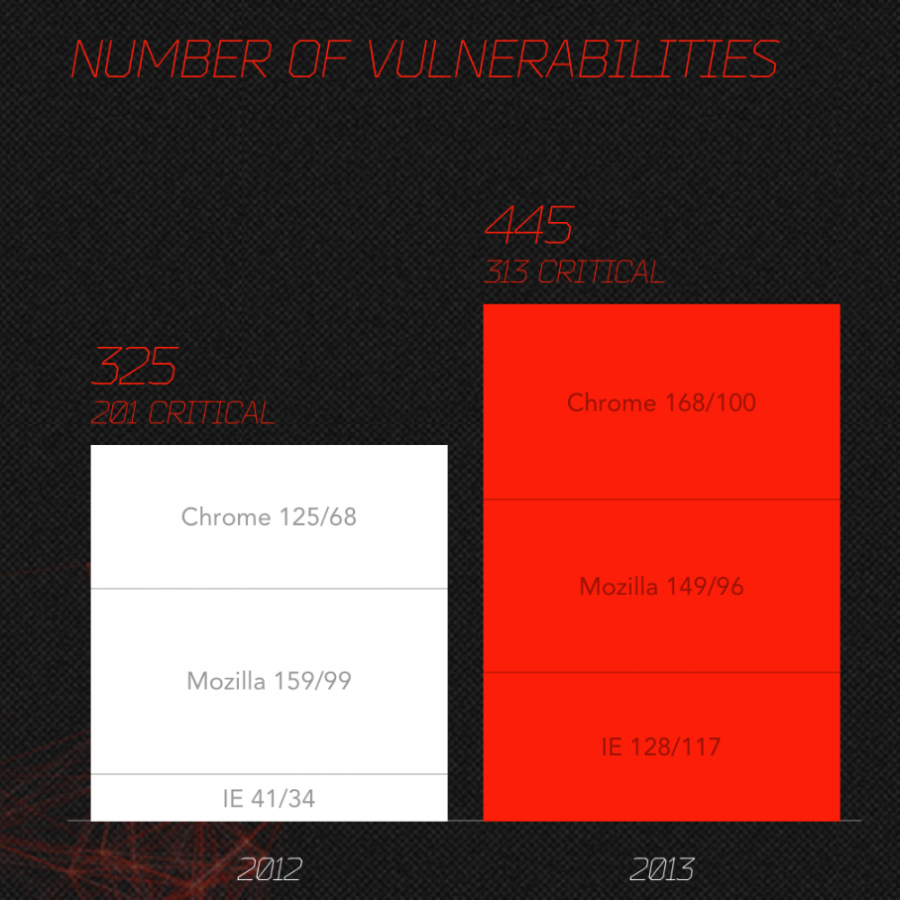
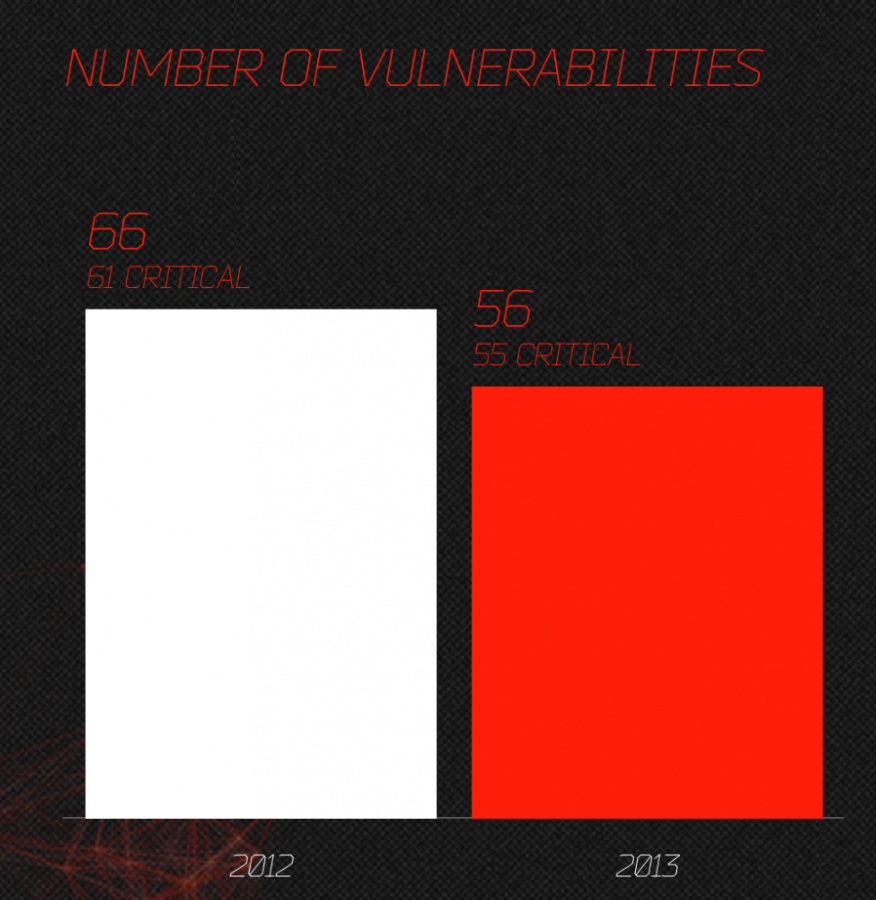
Browsers:
The vulnerability of the Mozilla browsers seems to start decreasing as its market share decreasing, while Chrome had about 50% increase due to its growing market share. Internet Explorer (IE) vulnerabilities on the other hand tripled from year to year, keep in mind that IE numbers include version 6 to 10. In another word, non-supported but still used versions.
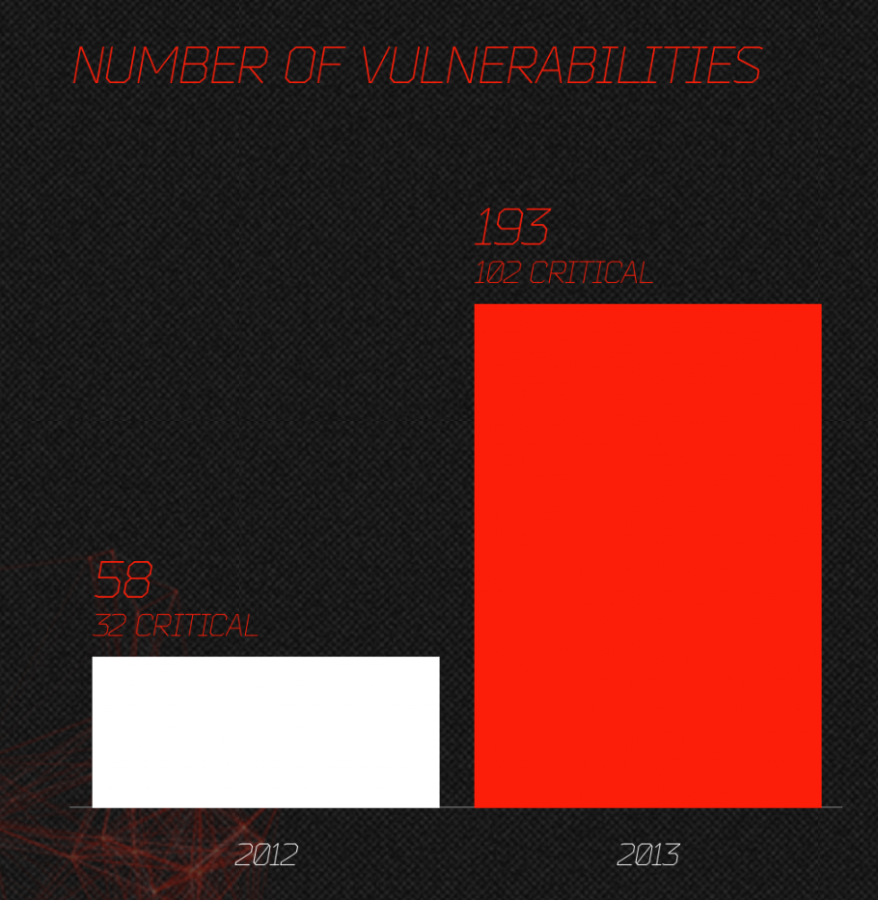
JAVA:
JAVA is one of the hackers favored applications, right after the Adobe software. It’s easy to program a JAVA applet and most people do have JAVA installed. It does help that the auto update feature is broken most of the times and the security updates aren’t as frequent as they should be.
Adobe Acrobat Reader:
The Adobe Acrobat Reader is probably the hackers most favored application. Practically everyone with computer has this application and Adobe isn’t known for creating secured code and/or releasing security patches in a timely manner.
Adobe Flash:
The number of Flash Player vulnerabilities had actually decreased from year to date. That’s good news, but mainly due to the news that Adobe had announced that stopped developing flash for the mobile platform. The replacement for flash will be HTLM version 5 and Adobe AIR. Hopefully, the desktop platform will be the next where flash disappears.
There are other hackers favored applications, such as Microsoft Office, media players, etc., but these applications did not have the size of growth year-to-year as the applications listed above.
So, again, why is that important to know? Well, if you keep your operating system and applications up to date, you’ve just substantially decreased the chance of your system being exploited…