Browser activity tracking has been in existence since, well, we have browsers. The first tracking method had been based on browser cookies, that provided limited local storage of 4,096 bytes or 4K. For tracking and marketing purposes the provided provided by the cookie has not been sufficient and Local Storage Objects (LSO), or Flash cookies had made its way to the end user’s PC. This method required Flash installed on the PC and the end users had/have some control over the Flash cookies. These cookie types were tied to the individual site in question, in another word there has been no collection of tracking information from all websites into a central depository.
Centralizing browser tracking information was made possible by JAVA scripts and third-party provided services, such as Google Analitics (GA). Initially, Google’s “free” service was intended to webmaster and provided detailed website statistics for the sites that opt-in to this service. In the process, Google amessed a central depository of browser activity tracking information that proved to be valuable for advertisment purposes and as such, the information is being sold to marketing companies. The “free” GA is still available and most webmesters do use this service, that provides continuous update for Google’s central depository. Google actually derives 90-95% of their income from selling advertisers the collected information. There are number of other companies that rely on the same method for generating their income and collect browser tracking information without the end user’s consent.
Running hidden scripts on the end user’s system and collecting information about the end user at the very least is a privacy risk. The information collected may include sensitive private details, location, interests, age, sexual orientation, sexual habits, relationship status, religion, political views, health concerns, employment status, and more. Increasingly, the collected online information, or end user profile, is being correlated to offline information for better success rate of the advertisement campaign.
The profile based on Internet activities certainly can provide some benefits for end users and will trigger behavioral based ads showing up in the browser or email. If you’re looking for the item being advertised, you may even find this great or just cannot resist the sale price. The problem isn’t buying products on the web, rather the profile in itself. That profile maybe used by big corporations and health insurance companies to make decisions about you, that can literally affect your life and livelihood. You may not get the job where the interview went great, or your health insurance application is denied because of your “established” profile. This profile has its own life and the individual in the profile cannot change it easily, or at all.
The security risk isn’t that clear, but consider this. Hackers use the same iframe method to install malware on your computer. How it works is rather simple. The hackers gain control of the website and inserts an iframe, a.k.a. web beacon or one pixel white image, to the site’s HTTP code. The web beacon points to the malicious script, the browser downloads this script when the users visits the site, and executes it in the background on the unsuspecting end user’s PC. Much like how the tracking scripts work that also could be used for malicious purposes. In certain view, tracking scripts collecting privacy information about the unsuspecting end user is already malicious enough…
Disabling iframe will prevent tracking; however, the Internet browsing experience will suffer greatly. So, what can you do to prevent companies tracking your Internet activities?
The Do Not Track (DNT) HTTP header standard will not prevent advertisers collecting information about as posted earlier. The proposed DNT standard is heavily influenced by advertisers and as such, it protects their interest and does not care much about the end user’s privacy.
The tracking companies have a standardized method for calling and executing their scripts hidden from the end users. The method is basically an HTTP link that includes the website’s identification number. For example Google’s JAVA script is referenced as:
“google-analytics.com/ga.js”
try {
var pageTracker = _gat._getTracker(“XX-0000000-0″*);
pageTracker._trackPageview();
*Actual site ID number is removed and the full script is not shown
For people who do not want to have their Internet activities tracked, there are free browser add-ons that blocks known tracking company scripts being executed. While it is a possibility that these add-ons track browser activities, nonetheless, they do block about 1,400 known tracking companies from collecting browser activity information.
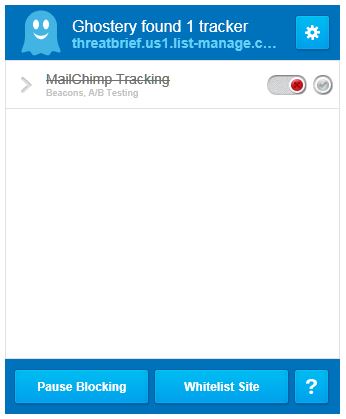
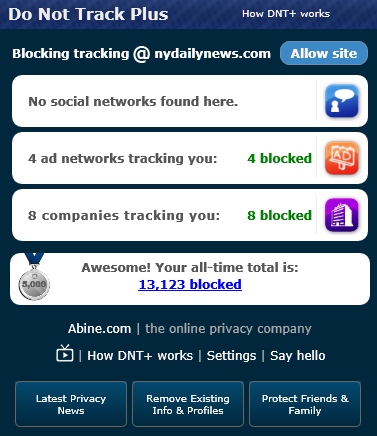
The Do not Track Plus is a corporation supported closed source browser add-on that will block tracking companies from collecting end users’ information. DNT+ should not be mistakenly identified with the proposed DNT standard; while the naming can be confusing, they have no relation whatsoever. DNT+ does actually block tracking and end user controlled vs. DNT that is voluntery at the current time and does not provide end user control. The interface displayed on the left is pretty straight forward. DNT+ can block social networking site tracking, advertisement company, and tracking company scripts. The configuration is pretty simple, under “Settings” just click on “Block all” and you’re done. DNT+ also displays the number of tracking scripts that has been blocked. And yes, the more than 13,000 number is correct and had been reached after about three month.
DNT+ is available from Abine free of charge and currently supports Firefox, Internet Explorer, Chrome, and Safari on Windows and MACs. DNT+ currently does not have mobile device offering, but it’s in the works.
The automated installation package can be downloaded here
Ghostery is a community supported open source browser add-on that is also available for free. It supports all major browser for PCs and MACs.
The interface displayed on the right isn’t as “pretty”, but just as effective as DNT+, if not more. The configuration is simple, just select “Block all” within the “Settings” pages and it will block all known tracking scripts.
Ghostery does not display the number of scripts that had been blocked. This might be beneficial for the end users since this number can also be used for tracking purposes. One benefits of Ghostery is the knowledge pages that displays a number of interesting information about the tracking company. Among other information, the knowledge page displays the type of information collected, retention and sharing policy, privacy policy link, the number websites using the tracking company, etc.
Ghostery installation source can be downloaded from here
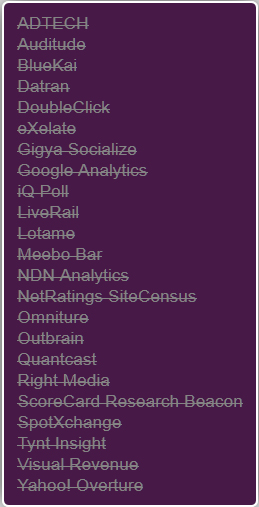
The images display the number of tracking companies being blocked when visited a single web page. Why there are so many companies tracking a single page?
The answer is how the web page in question had been created. Most web pages nowadays utilize “iframe” to insert contents from other websites without actually writing the content. When these other contents inserted in the visited page, they also load their tracking companies’ scripts as well. In another word when a single page is visited, there might be 10-15 other pages visited and the same number of blocked tracking scripts show up in these browser add-ons.
It is up to you, if you want blocking these tracking scripts. While certainly tracking companies already have your profile; however, stale profile is not valuable for marketing companies. As such, stale profiles are removed from their central depositories even it is not actually deleted.
Warning: Neither of the browser add-ons will block hacker’s scripts, they only block known ad, social networking, and tracking companies’ scripts.